
Overview
Cyber warfare is fought today on an asymmetric battlefield in which the odds are often stacked in favor of an agile and anonymous adversary. Existing defensive technologies such as antivirus, intrusion detection, and code-hardening toolchains can only partially level the field. Technical gaps in these defensive technologies are evidenced (1) by the typically large latencies between the occurrence of cyber-attacks and their eventual detection and remediation; and (2) by the failure of existing technologies to perform mission-centric threat impact analysis.
CRATE provides new tools and techniques to extract real-time human-actionable intelligence about the mission-level impact of cyber events detected within complex architectures.
Operation
A CRATE concept of operation is shown below in Figure 1. The diagram depicts three core capabilities of the CRATE system. Firstly, CRATE provides a framework for gathering large quantities of real-time metrics generated by cyber-sensors on disparate hosts. Secondly, CRATE uses machine learning to identify cyber events within the metric streams and aligns these events to the lifecycle of a cyber-attack. Finally, CRATE utilizes this alignment to determine the mission-level severity and impact of the attack—for example, a mission that depends heavily on near real-time ISR would be severely impacted by a Denial of Service (DoS) attack against services providing that capability.
CRATE combines top-down and bottom-up modeling paradigms. CRATE’s top-down approach leverages industry-standard Mandatory Access Control (MAC) technologies such as AppArmor and SELinux and assumes that high-fidelity models of correct behavior are specified formally as engineering and design artifacts. When behaviors not explicitly allowed in these top-down models are observed, the system generates logs which are treated by CRATE as indicative of anomalous behavior, even when those behaviors are performed by privileged users.
Acknowledging the difficulty of specifying complete top-down models (and to address the possibility of resultant false positive anomaly detections), CRATE also incorporates a bottom-up noise reduction approach that learns correct behaviors by applying machine learning to sensor values and identifies aberrations observed during sliding windows of time.
CRATE provides visualizations and metrics that enable the operators of mission-critical cyber systems to answer the questions:
Similarly, CRATE allows the mission operators to answer the question:
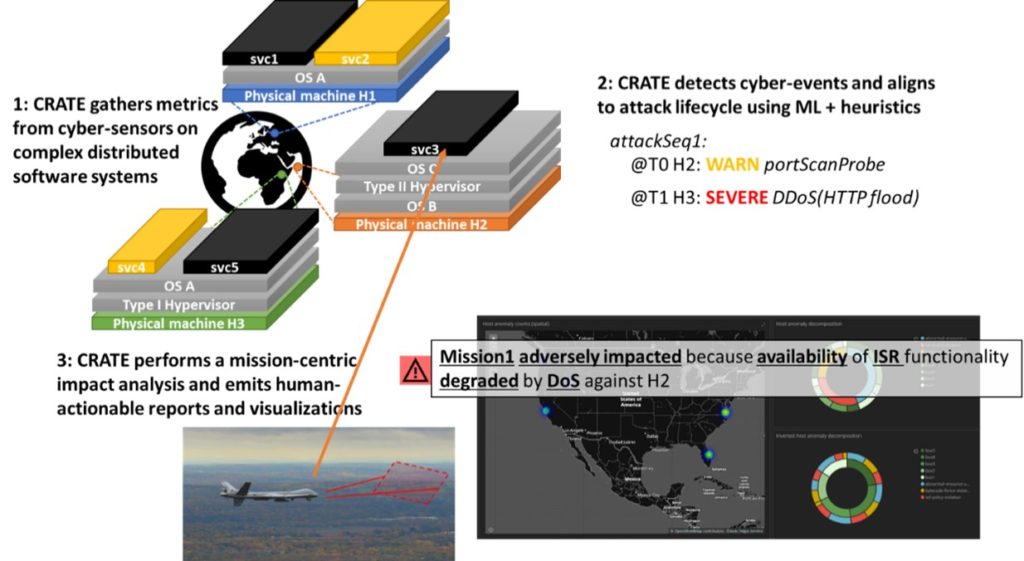
Figure 1: CRATE CONOPS
CRATE provides the following innovations over existing technologies: