
Rampart is focused on turning traditional DevOps environments into DevSecOps environments. Rampart is a next-generation code hardening tool that belongs to a family of technologies broadly referred to as Realtime Application Self-Protection (RASP). Rampart extends the RASP concept by using Learned Enforcement (LE-RASP) to ensure the correct behavior of software systems. Unlike traditional RASPs, Rampart uses machine learning over a training epoch to determine the behaviors representative of correct operation and to subsequently prevent emergent behaviors outside that envelope from executing.
Recent high-profile events have demonstrated the limitations of static code analysis, perimeter defenses, and monitoring tools. Rampart uses dynamic techniques to ensure that applications operate as designed and tested, including any third-party code they contain. Rampart provides this critical capability in a manner orthogonal to existing techniques to ensure that both legacy applications and future DevSecOps pipelines can operate safely in a cloud environment.
Rampart is a learning-based application fortification tool that prevents vulnerabilities in deployed software from being exploited by attackers. Applications are fortified by monitoring their execution in real-time and by blocking or alerting when behaviors occur that were not previously seen during a training epoch.
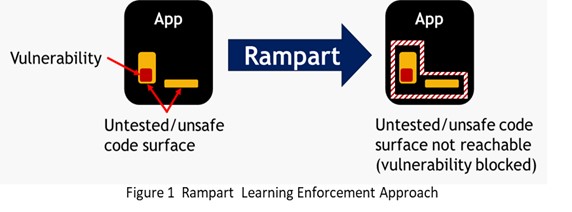 Figure 1 illustrates how Rampart provides a protective boundary at the application level that can immediately detect and respond to a security breach.
Figure 1 illustrates how Rampart provides a protective boundary at the application level that can immediately detect and respond to a security breach.
During training, Rampart curates’ sequences of application control flows, lifecycle events, and platform interactions into a model of “normal” system behavior. During enforcement, Rampart continuously compares the observed behavior of the system against this learned behavior model and when discrepancies are discovered, a Rampart runtime sensor generates alert telemetry and/or blocks problematic behaviors before they can be used by attackers to break into the system or damage its state.
Unlike most other cyber-sensors, which operate on platform-level events, Rampart tracks the actual control flow paths reached within an application as it runs. It can therefore detect bugs in logic for handling seldom-reached corner cases, such as the Remote Code Execution (RCE) vulnerability in Apache Struts, that led to the infamous 2017 Equifax breach. Rampart can also detect SQL injection attacks, logic bombs, and a slew of other issues that arise from the deployment of poorly tested or poorly authored code. Rampart provides a true zero-day attack prevention capability by blocking unwanted behaviors in an exploited system at their first point of occurrence.
Rampart alerts operators and blocks untested/unusual program behaviors at runtime before they can be exploited